"Microsoft Defender for Cloud has detected suspicious activity in your environment"
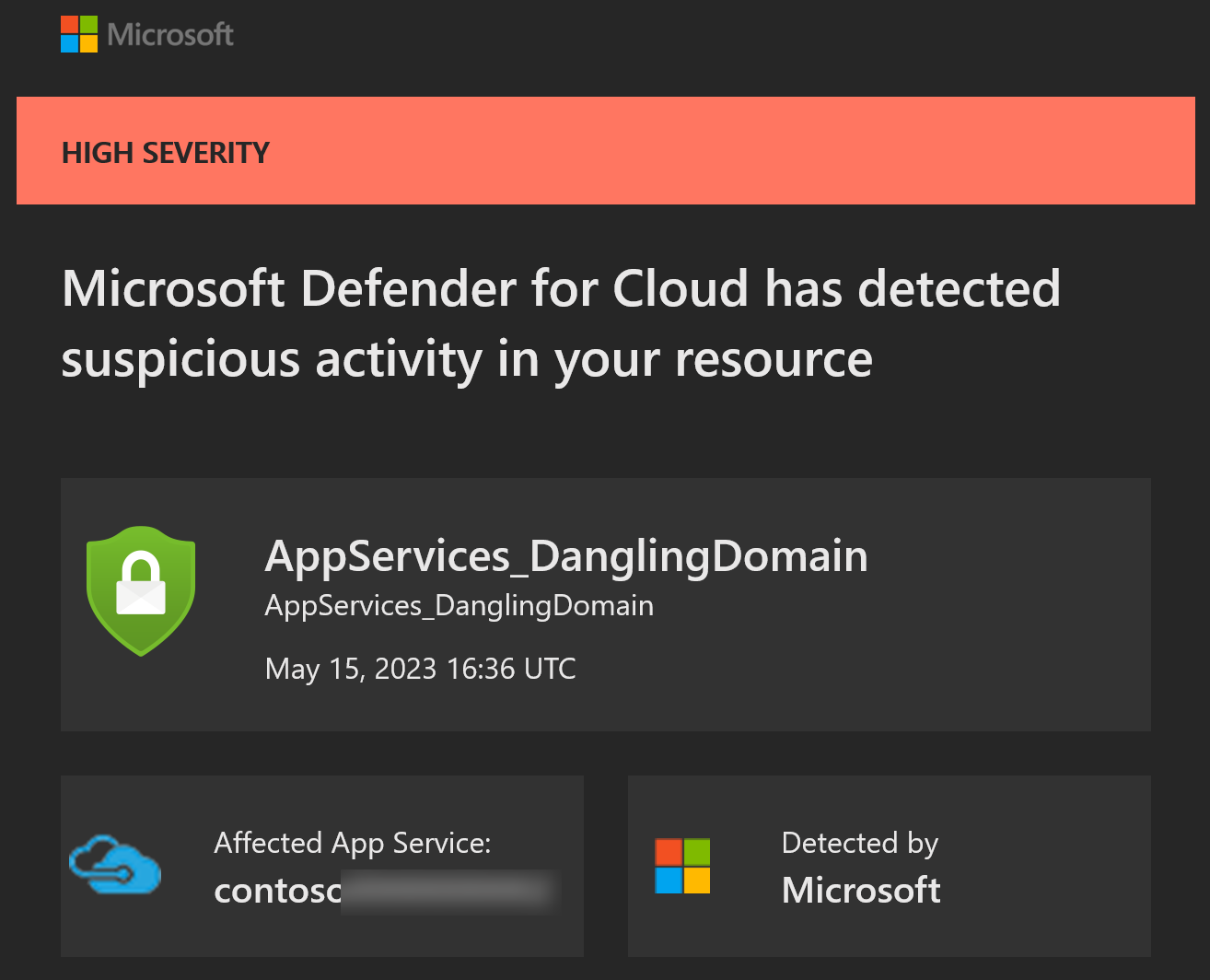
Posted on: November 13, 2023You might have received emails from “Microsoft Defender for Cloud” like this:
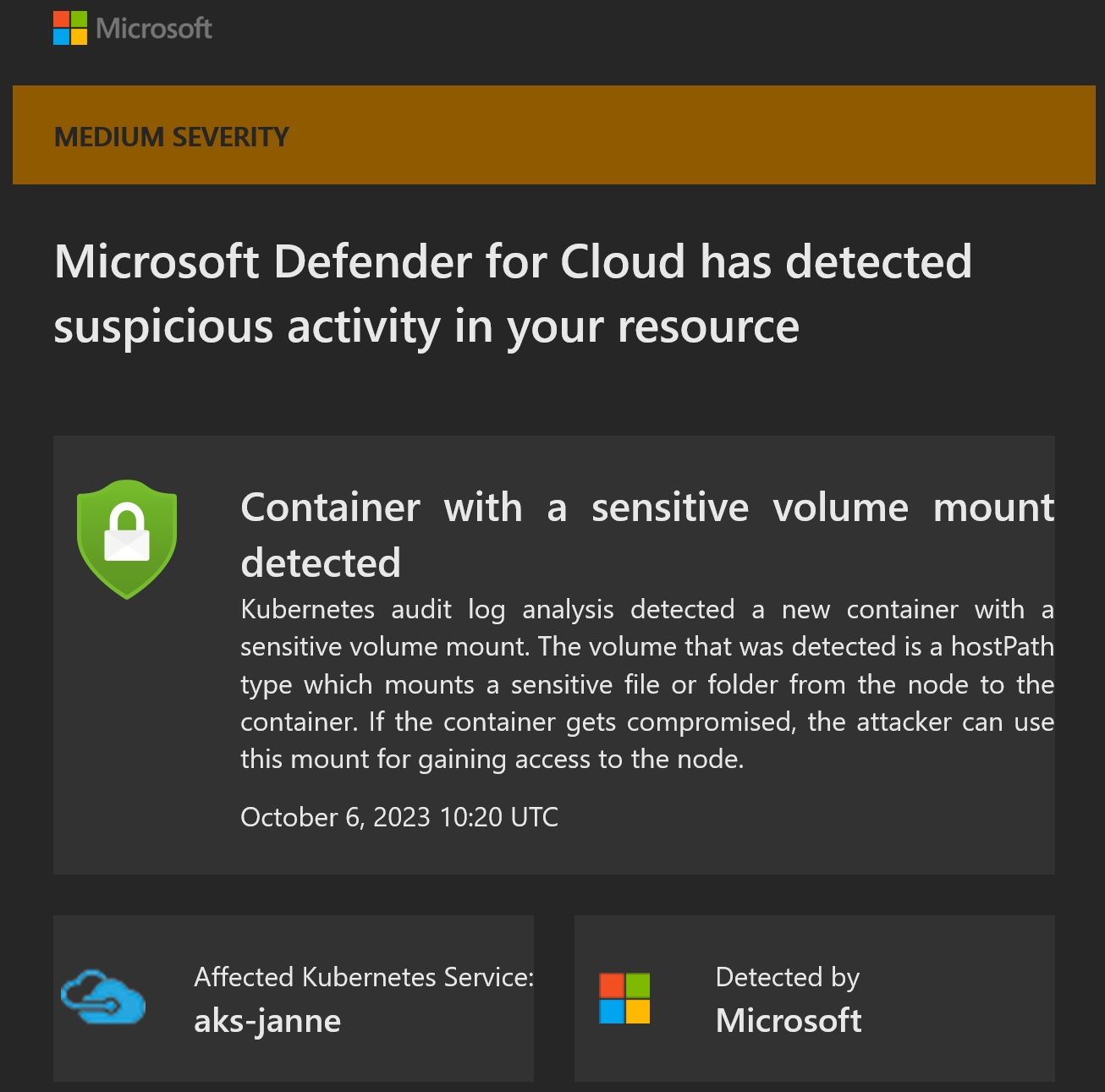
or like this:
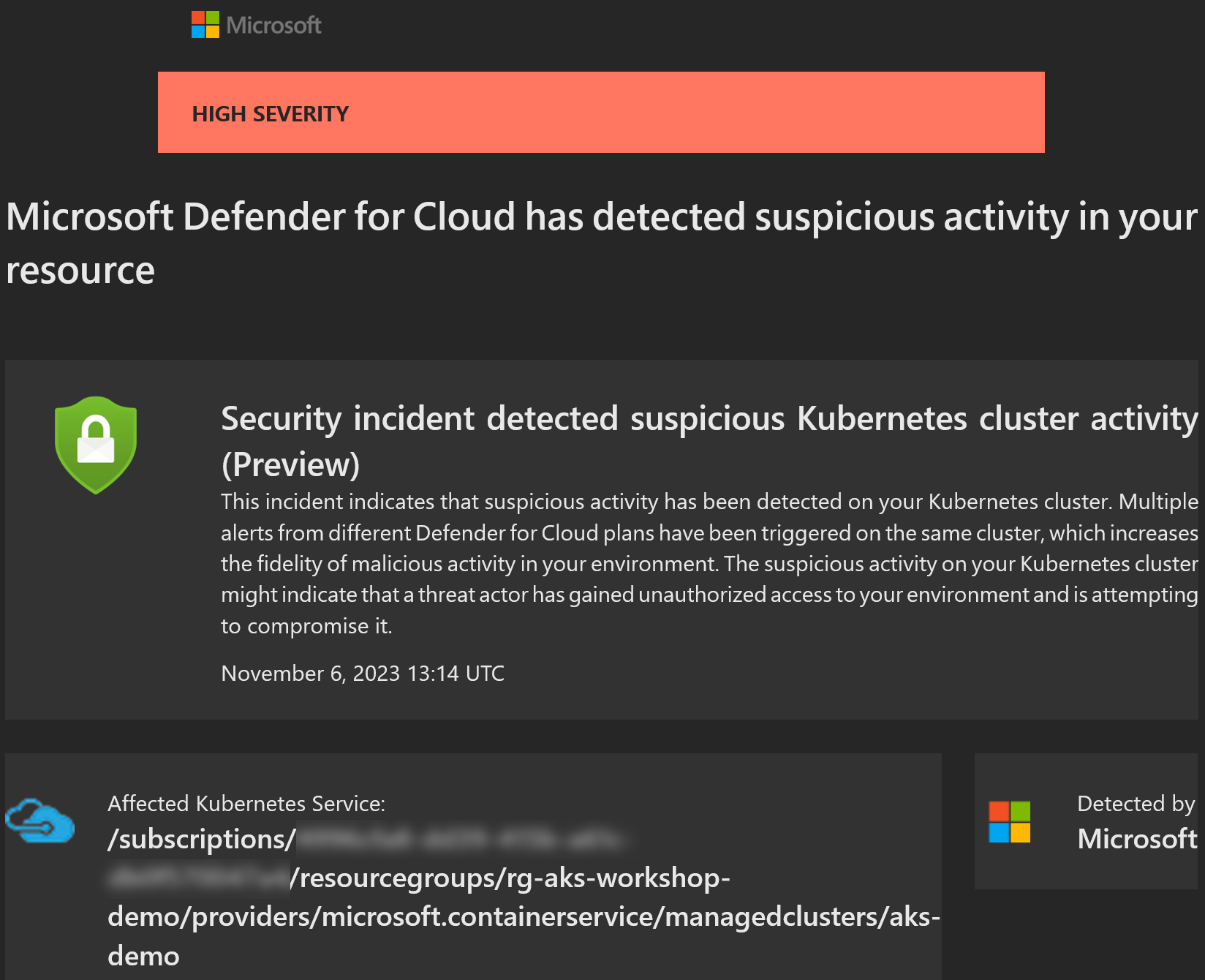
or one with extra bonus twist and multiple alerts from a single cluster in one email:
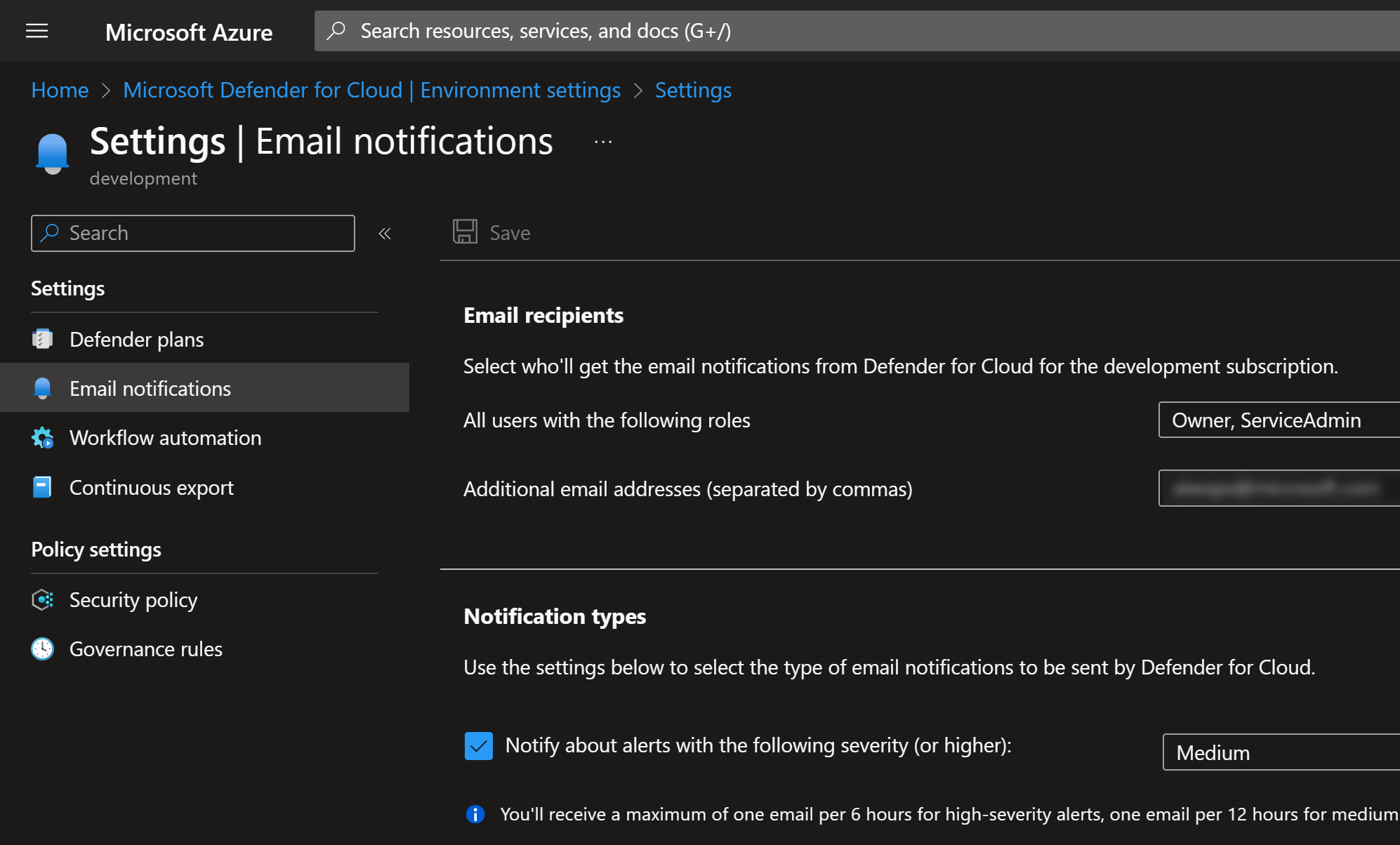
and if you haven’t, then please go to:
Microsoft Defender for Cloud > Environment settings > Select subscription > Email notifications
and validate that your email notification settings are correctly set:
after that you should go to:
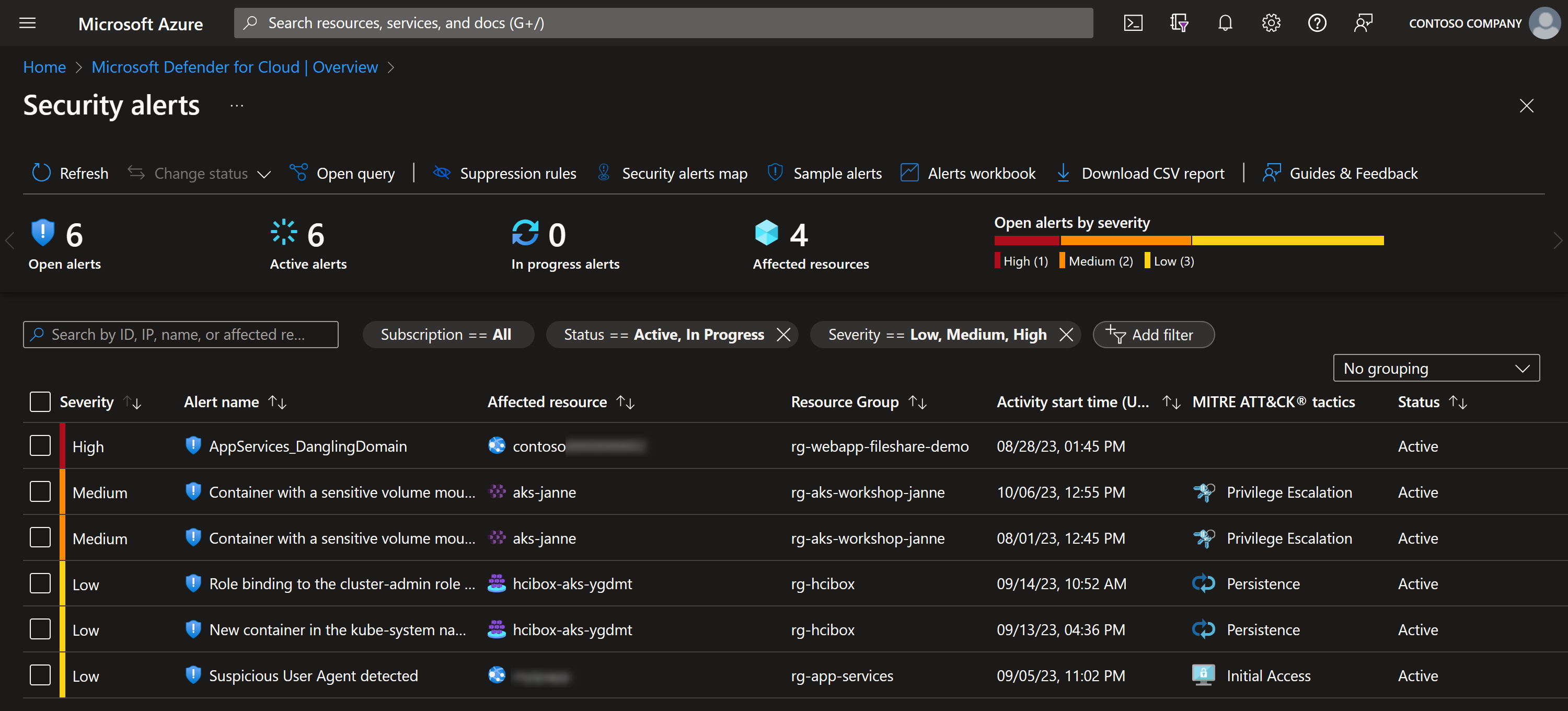
Microsoft Defender for Cloud > Security alerts
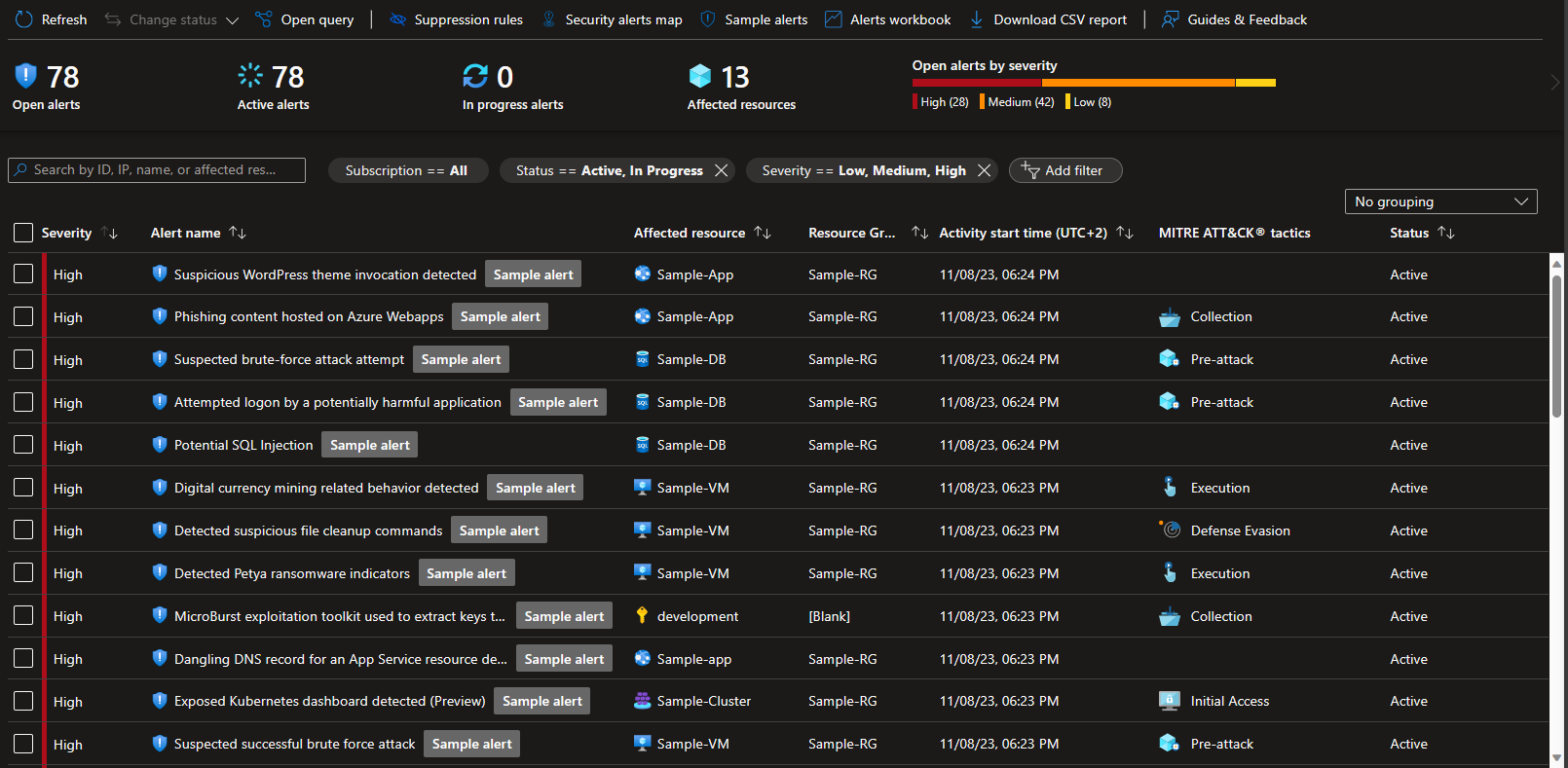
and see your “Security alerts” list in case you have not noticed them before:
and if you for some reason haven’t yet enabled Microsoft Defender for Cloud, then now is a good time to do that.
Microsoft Defender for Cloud > Environment settings > Select subscription > Defender plans: Enable all plans or select all the plans that you want to enable.
More information can be found here: Connect your Azure subscriptions.
But let’s get back to the list of alerts above. It does look bad, doesn’t it? Let’s go through them one-by-one.
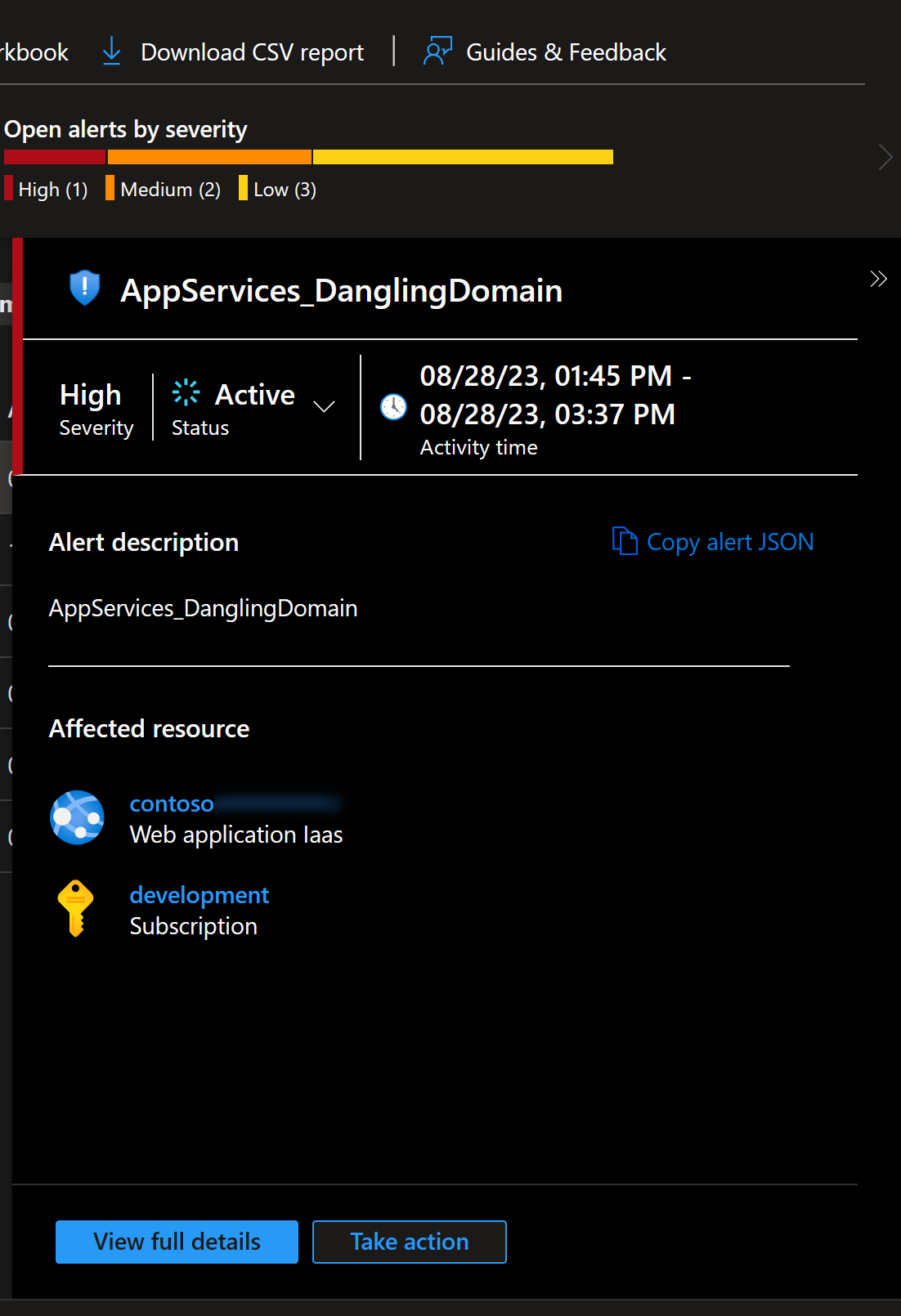
Dangling domain
I use Azure App Service a lot. It’s my go to service for hosting web applications.
Quite often, I use custom domains in my demos to match customers testing scenarios. Things are always a bit harder if you have your own domain and then you need to use your own certificates etc.
Of course, I do clean up environments after demos, but cleaning up DNS Records might be something that I forget to do. And that’s exactly what happened here. I had created app service with custom domain and then I had deleted it, but I had forgotten to delete DNS Records associated with it.
More information about App Service introduces dangling DNS protection and Alerts for Azure App Service.
So, I went to DNS zone and deleted the old record. Problem solved!
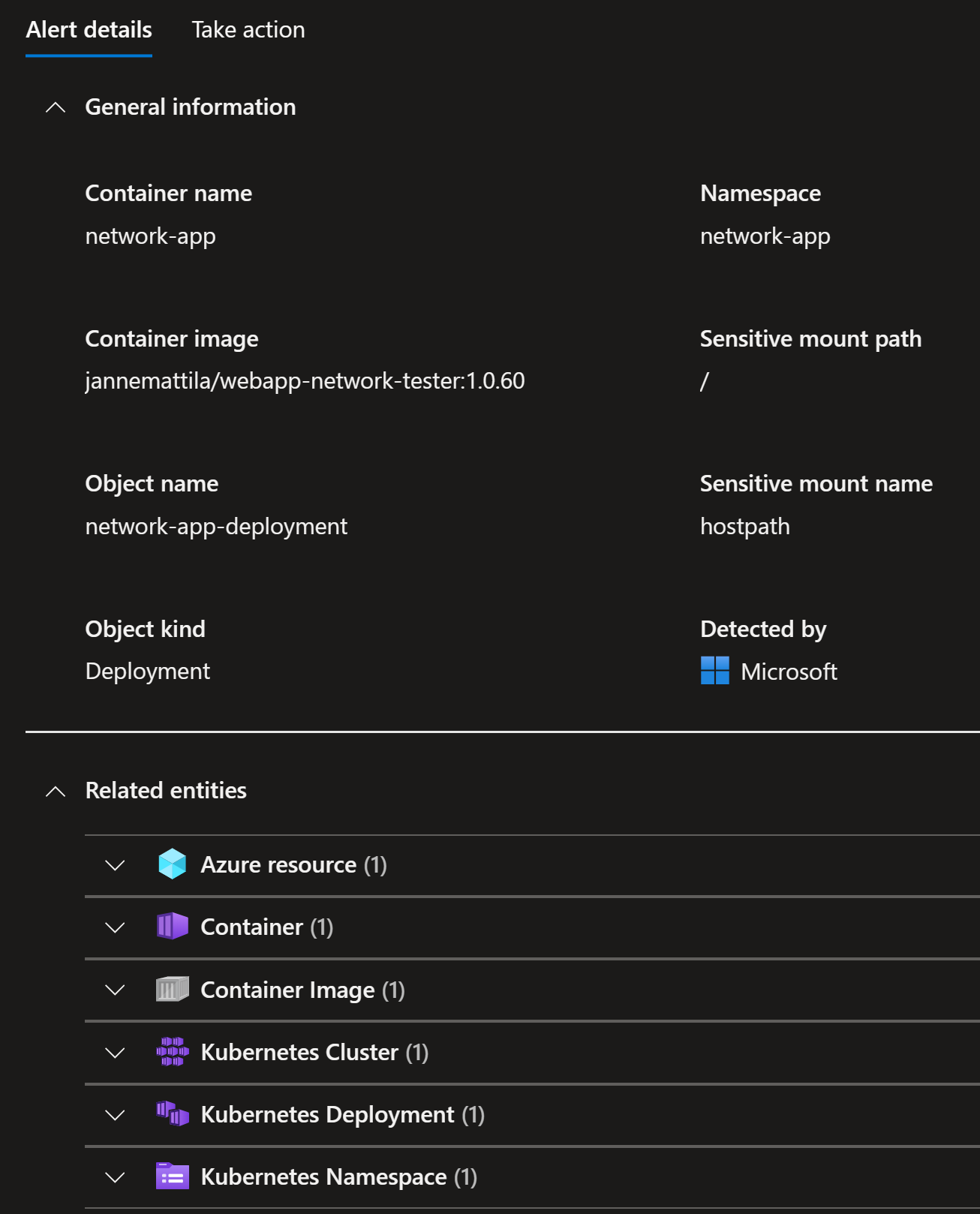
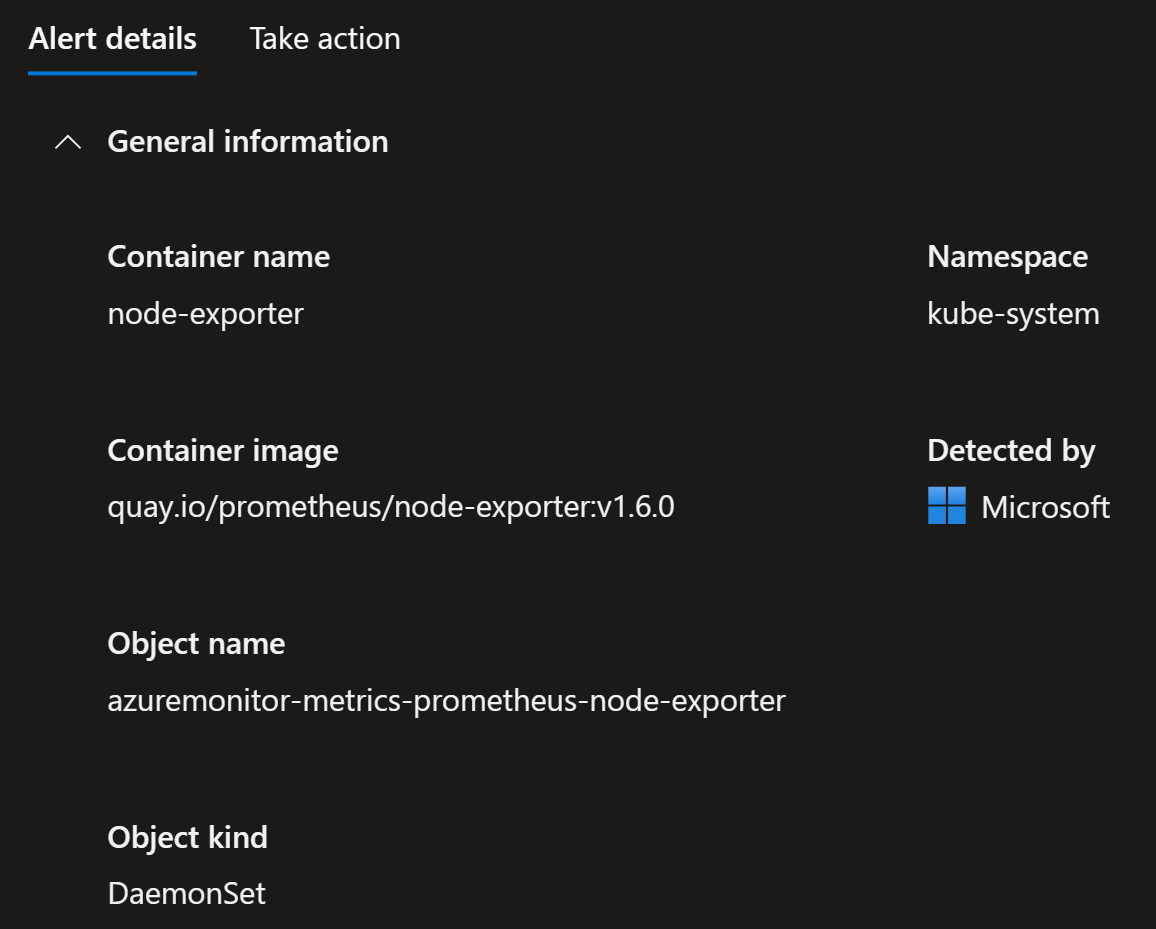
Sensitive volume mount
Azure Kubernetes Service is a service that is used by many of my customers and it means that I actively work with it. Therefore, I have created a lot of demos around it including Microsoft Defender for Cloud. This alert wasn’t a surprise, since I have caused it on purpose by adding hostPath to my demo deployment:
apiVersion: apps/v1
kind: Deployment
metadata:
name: network-app-deployment
namespace: network-app
spec:
replicas: 1
selector:
matchLabels:
app: network-app
template:
metadata:
labels:
app: network-app
spec:
nodeSelector:
kubernetes.io/os: linux
containers:
- image: jannemattila/webapp-network-tester:1.0.60
name: network-app
resources:
requests:
cpu: 100m
memory: 100Mi
limits:
cpu: 150m
memory: 150Mi
ports:
- containerPort: 80
name: http
protocol: TCP
volumeMounts: # <--
- name: hostpath # <--
mountPath: /mnt/host # <--
volumes:
- name: hostpath # <--
hostPath: # <--
path: / # <--
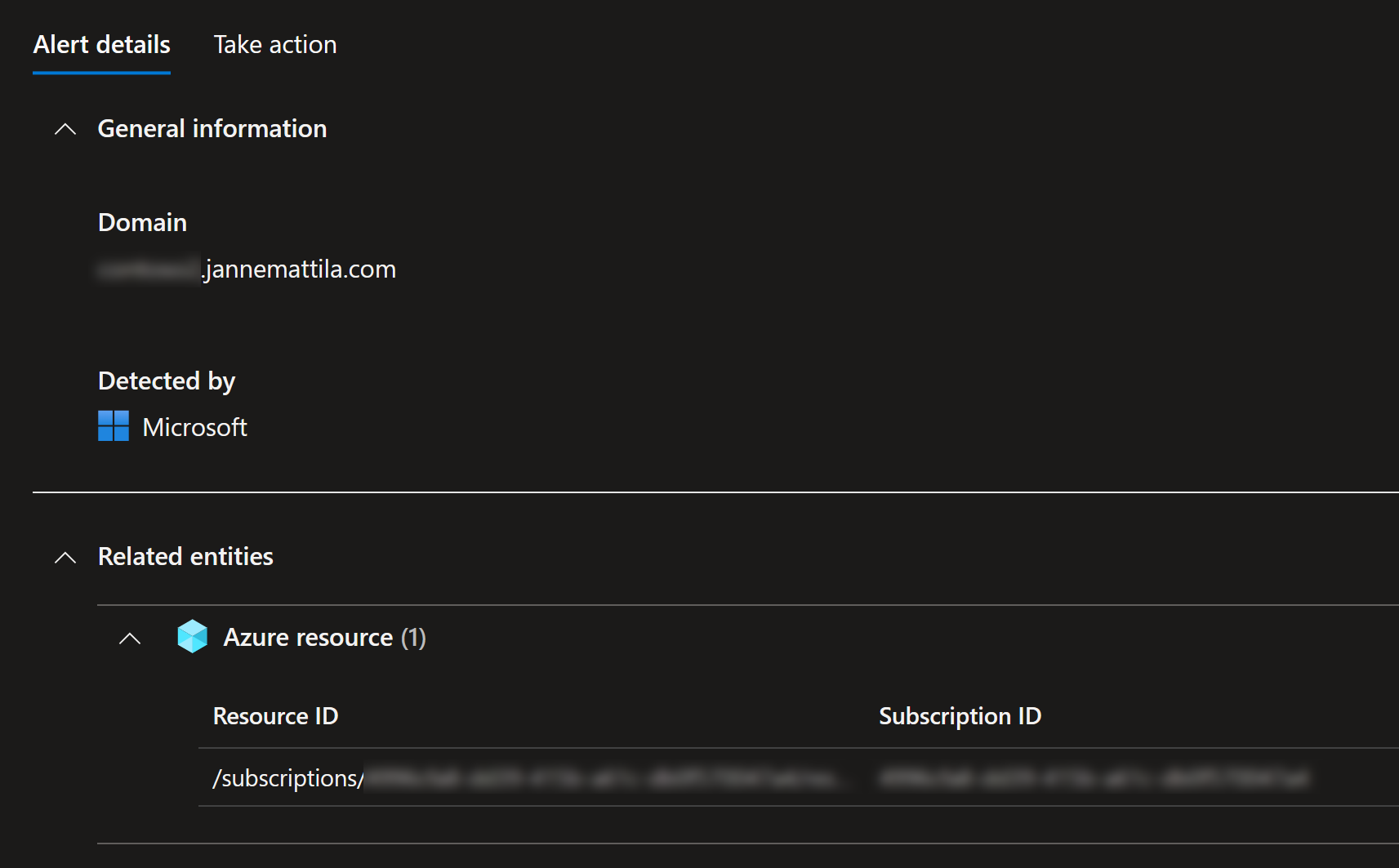
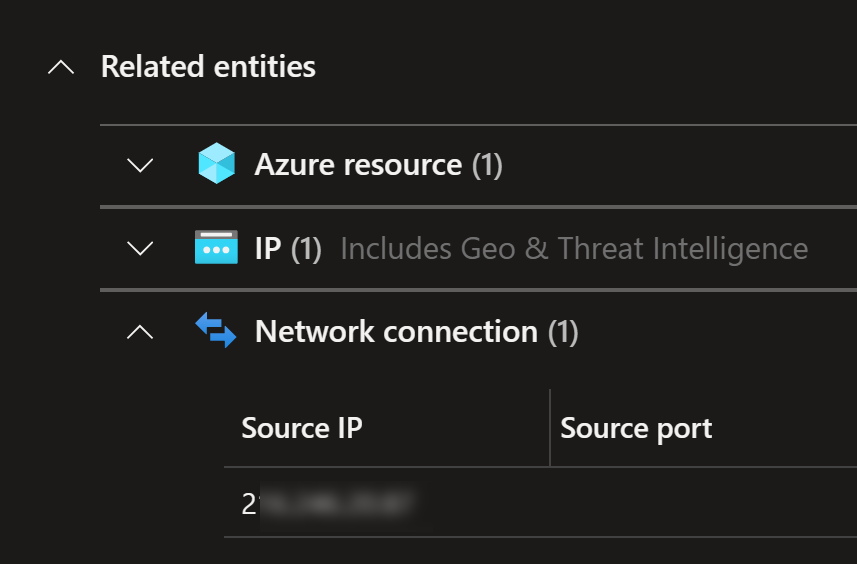
Microsoft Defender for Cloud alerts about this:
It also provides all the details needed to take corrective actions:
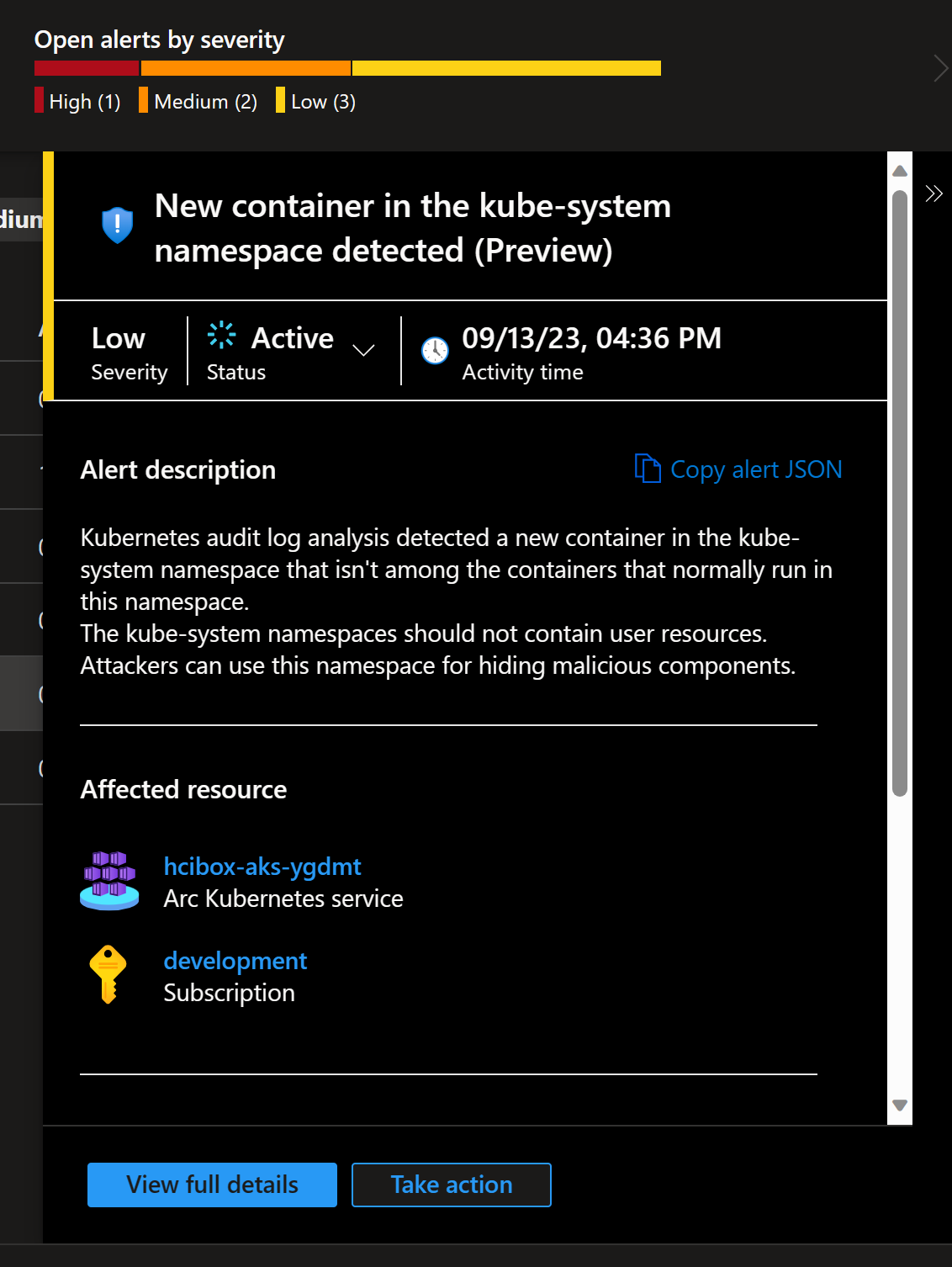
HCIBox related alerts
In my previous post Use HCIBox to learn Azure Stack HCI I wrote about how you can use HCIBox to learn Azure Stack HCI. Apparently, my demo environment had some issues and Microsoft Defender for Cloud highlighted them to me:
Since this is learning environment which I only deploy temporarily, I’ll just mark these as resolved:
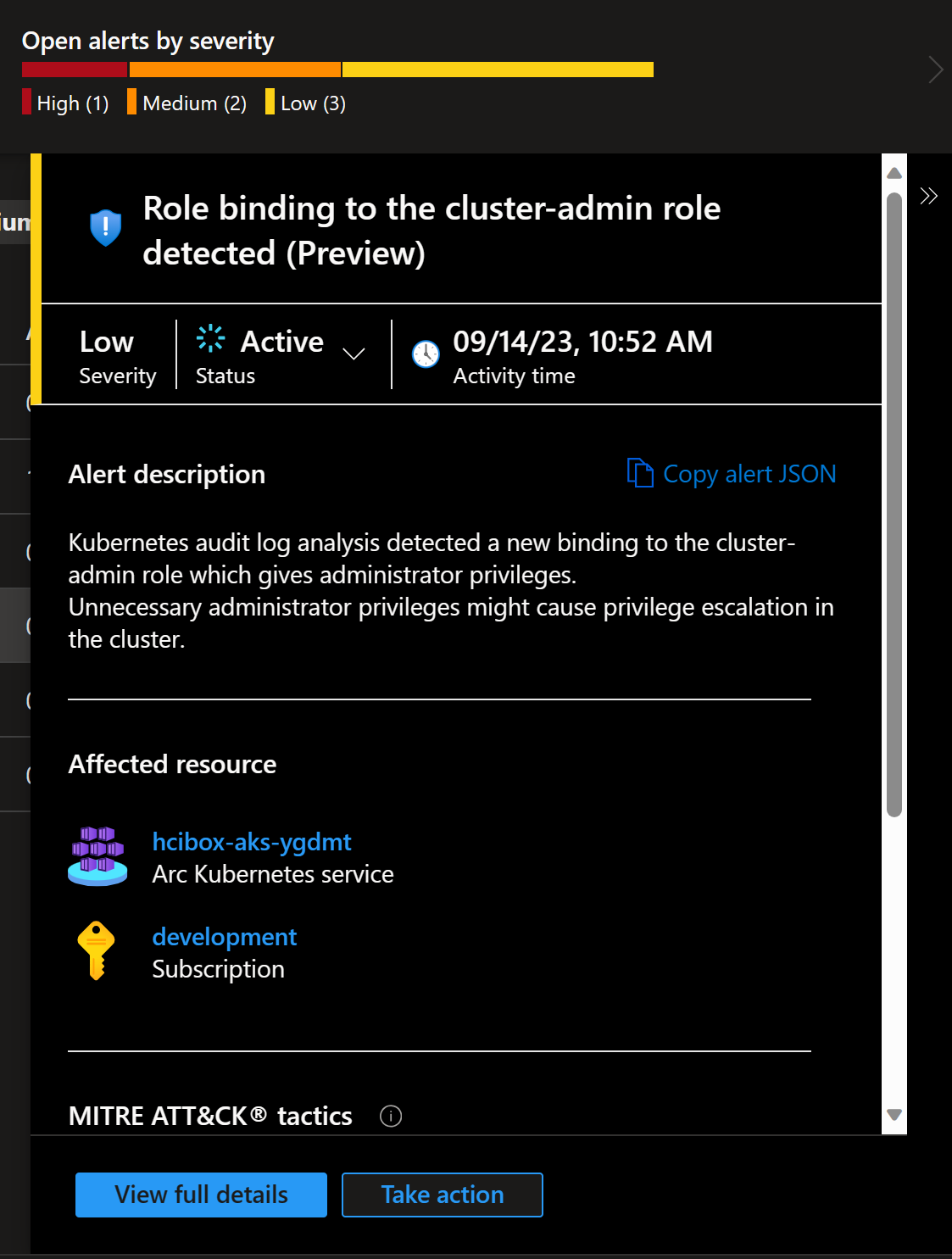
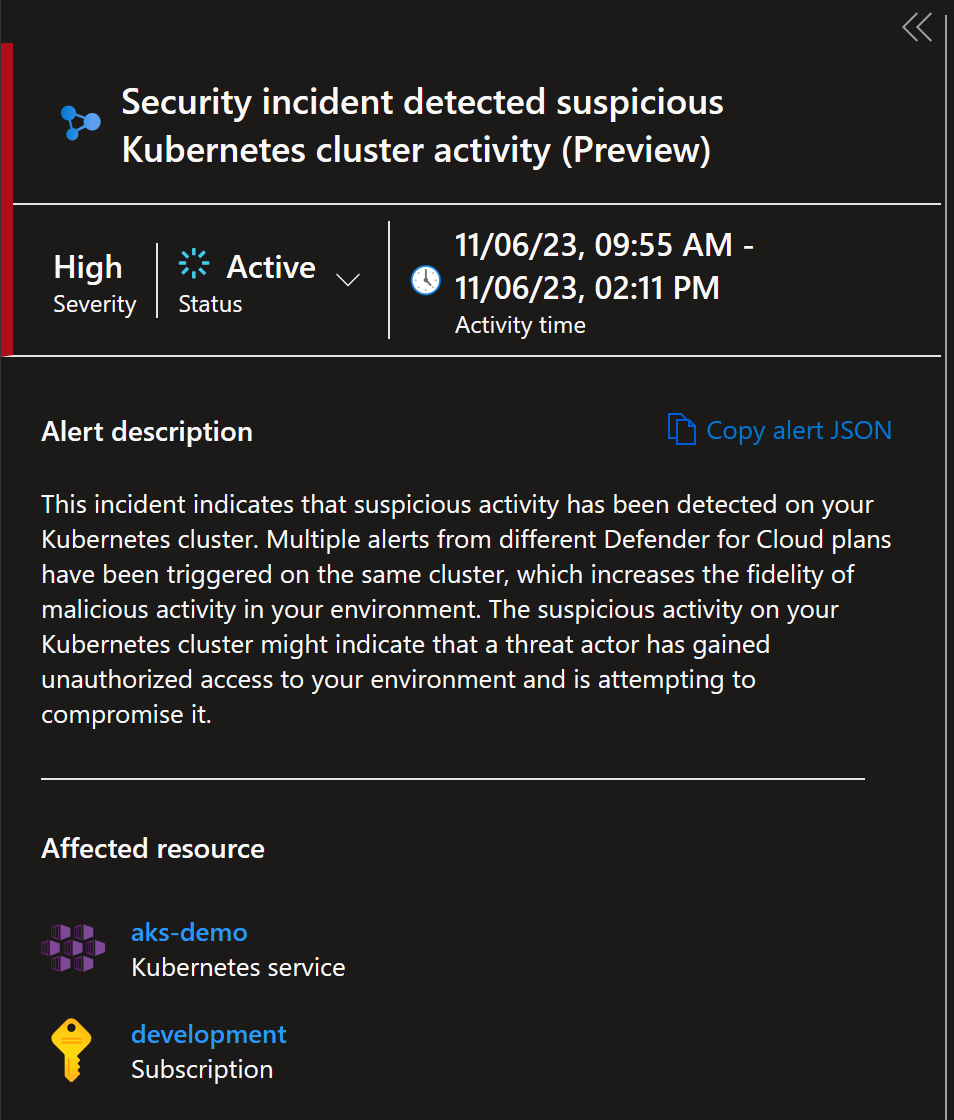
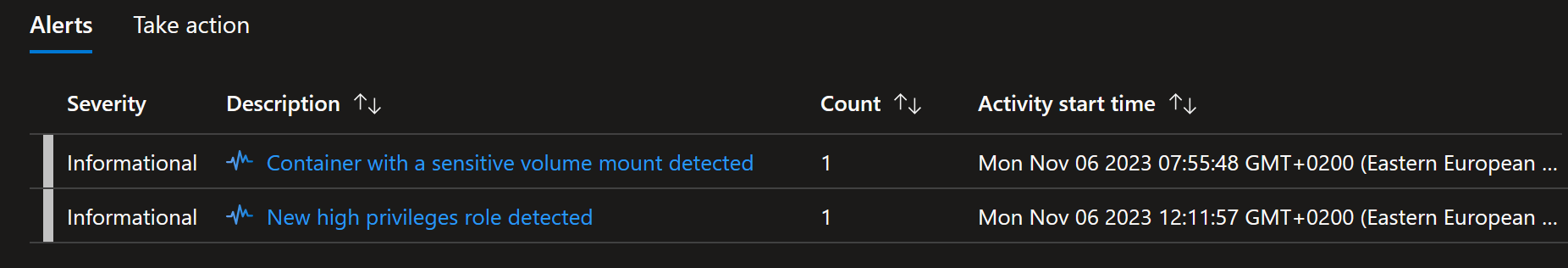
Multiple alerts from single cluster
This is something that I got after preparing for workshop about AKS:
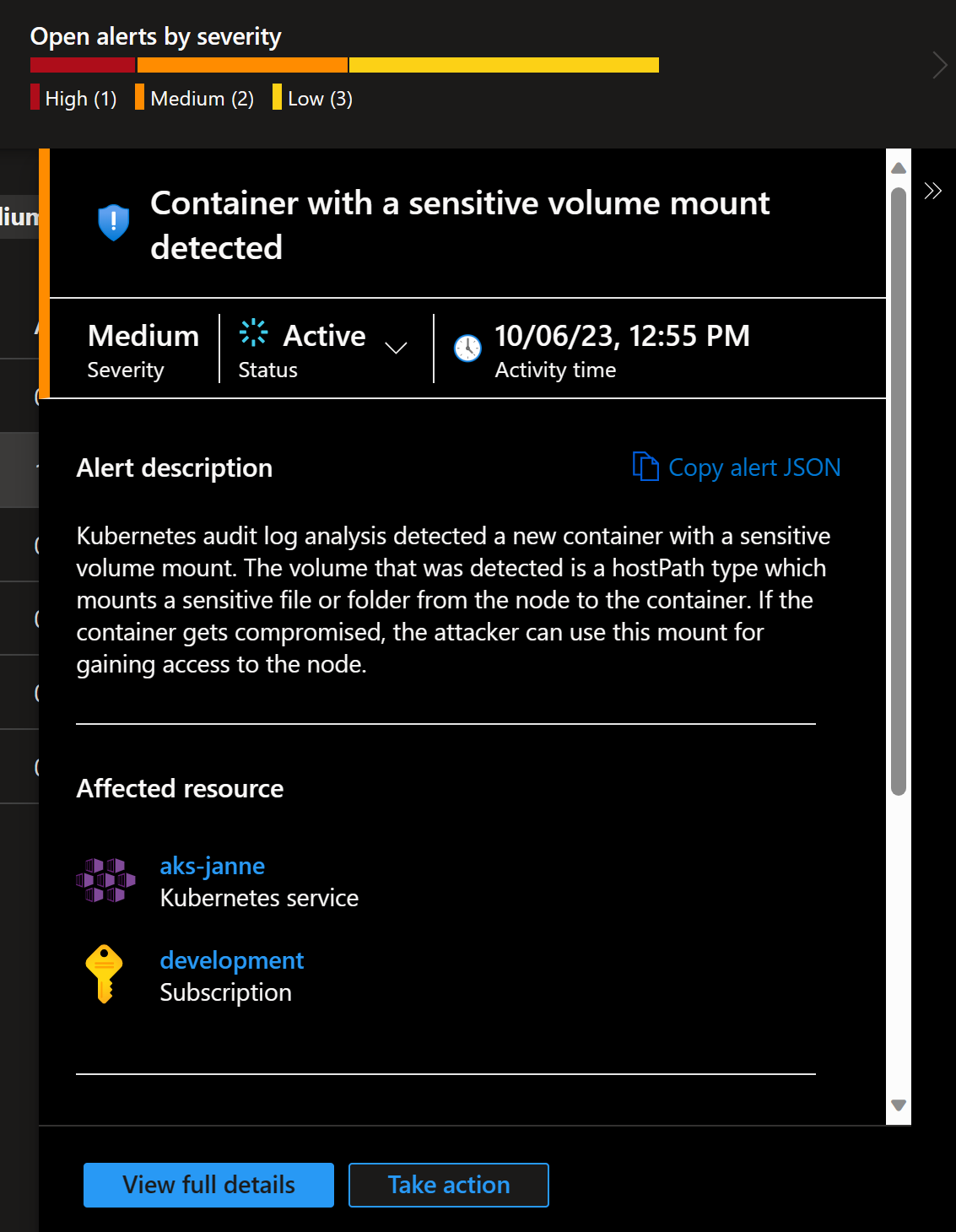
After opening the details, we can quickly see that sensitive volume mount
is also in this cluster:
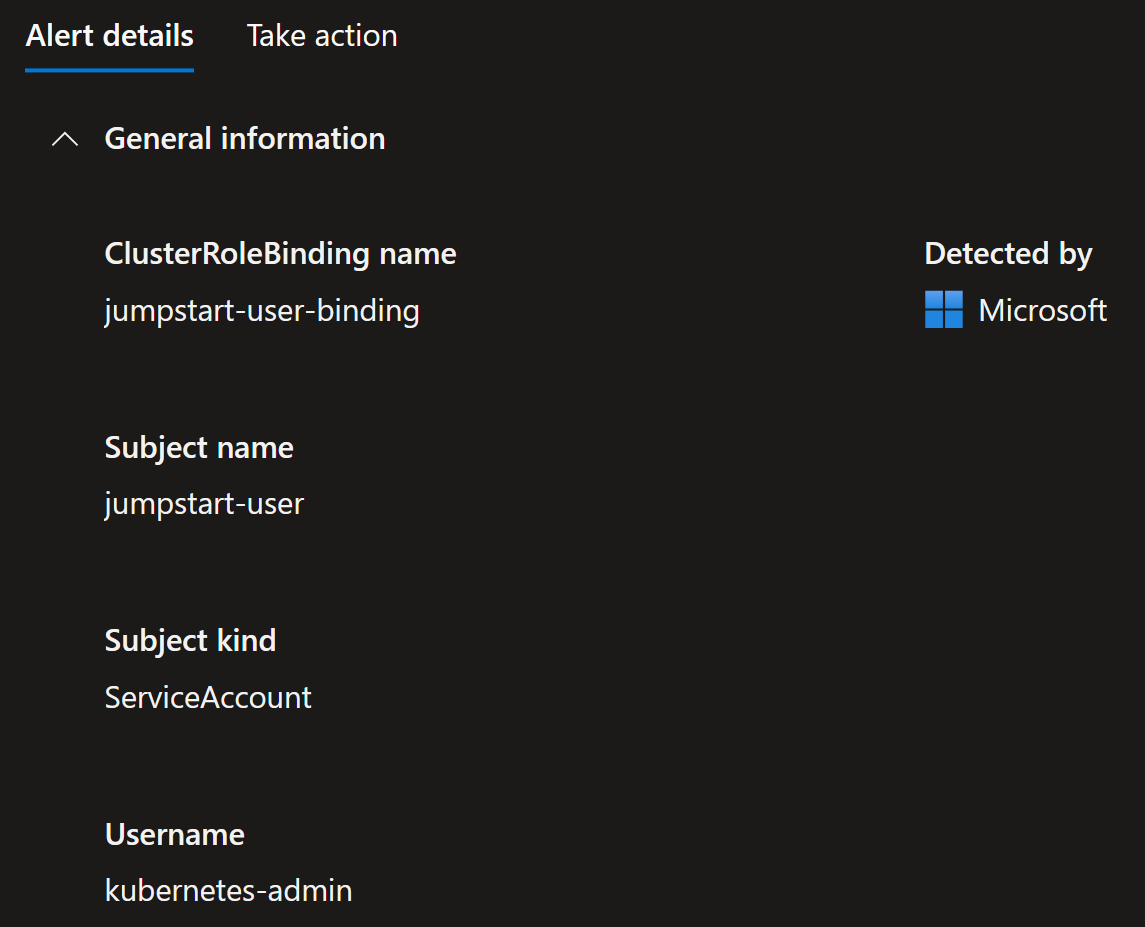
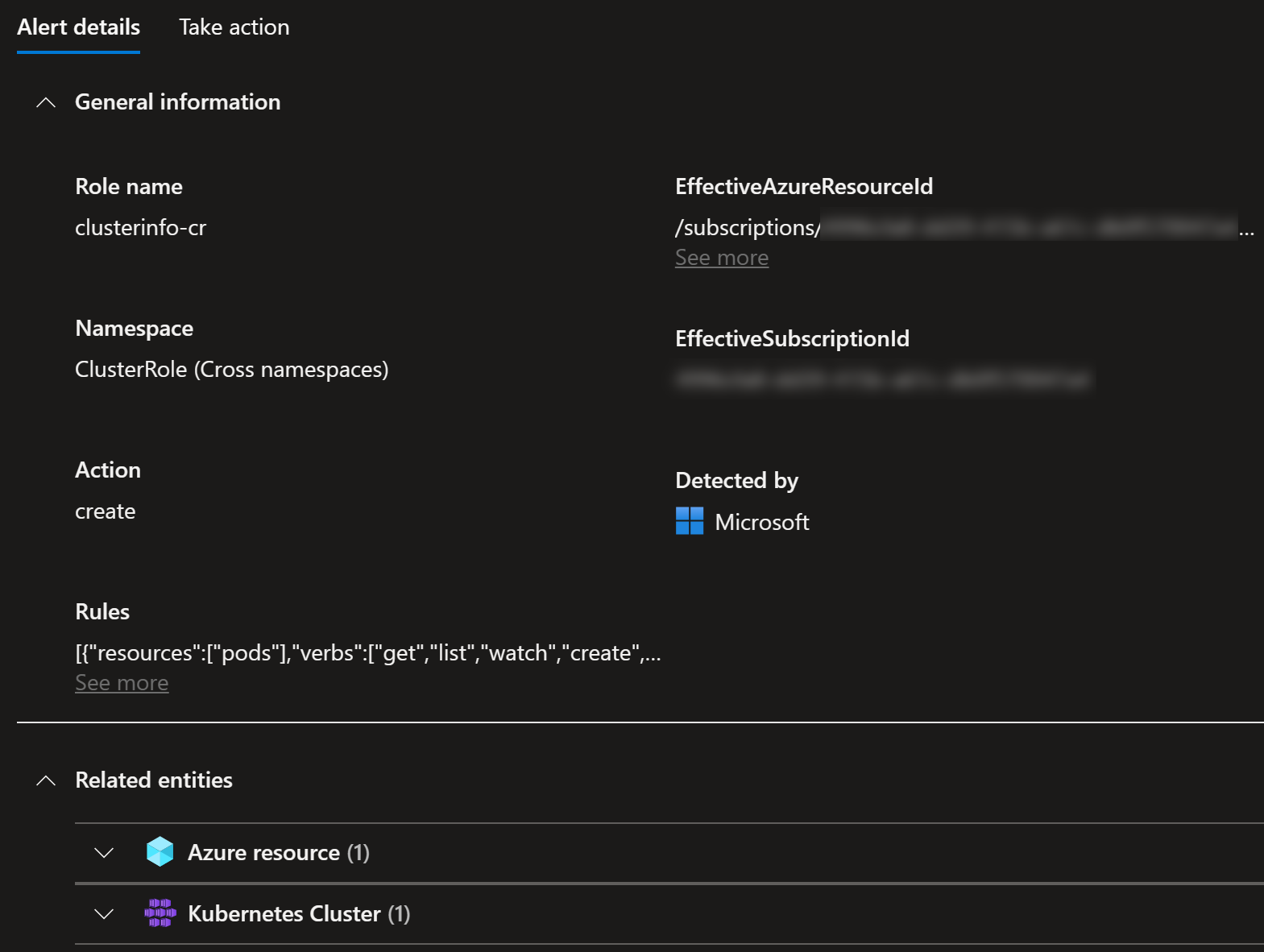
But the second one with New high privileges role detected was new one.
Opening details of the alert explains it right away:
So indeed, I’ve deployed ClusterInfo into my cluster using Helm:
helm repo add scubakiz https://scubakiz.github.io/clusterinfo/
helm install clusterinfo scubakiz/clusterinfo
I use it to demo the deployments so that it’s visually easy to see the changes using Cluster Info. Despite this alert, I recommend using it for learning purposes.
This AKS resource lifespan is only duration of one workshop, so I can dismiss these two alerts.
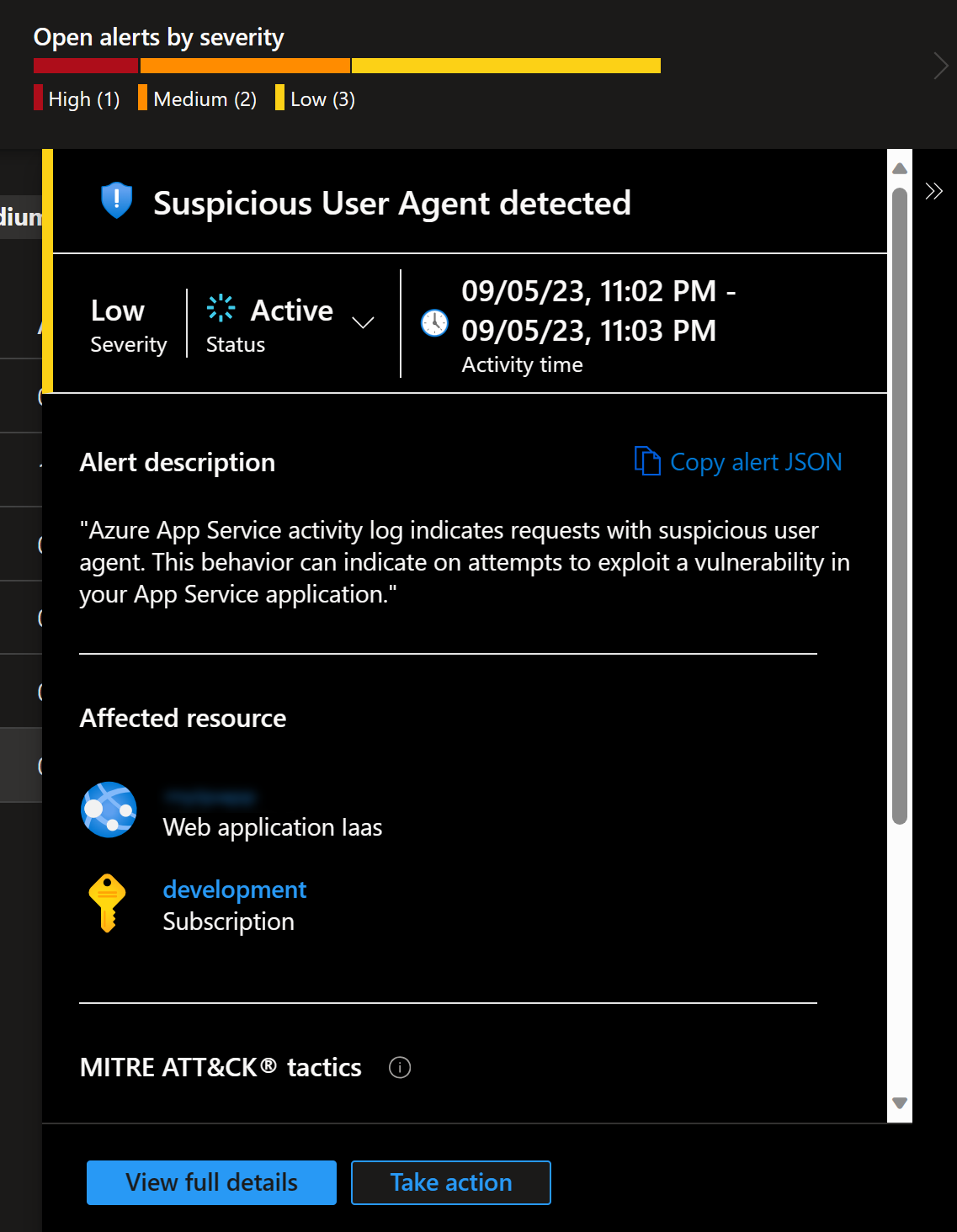
Suspicious User Agent detected
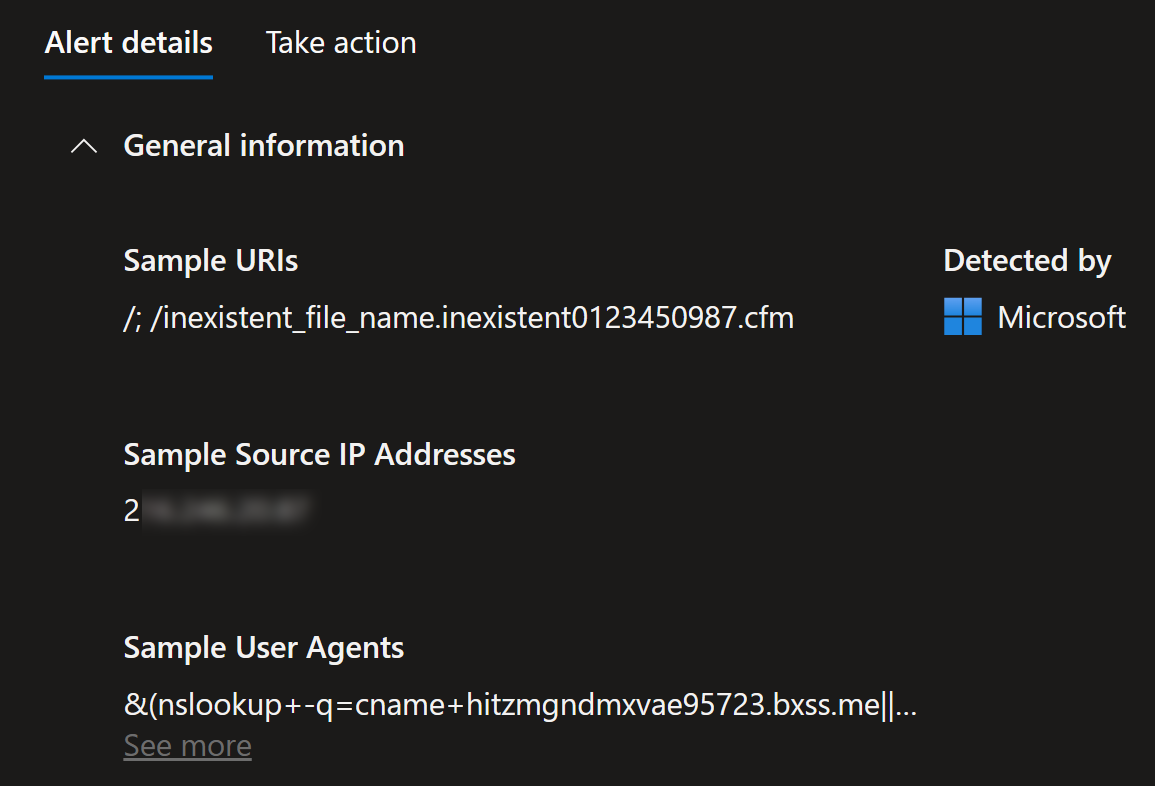
This one is an interesting one. Clearly something is scanning my web application:
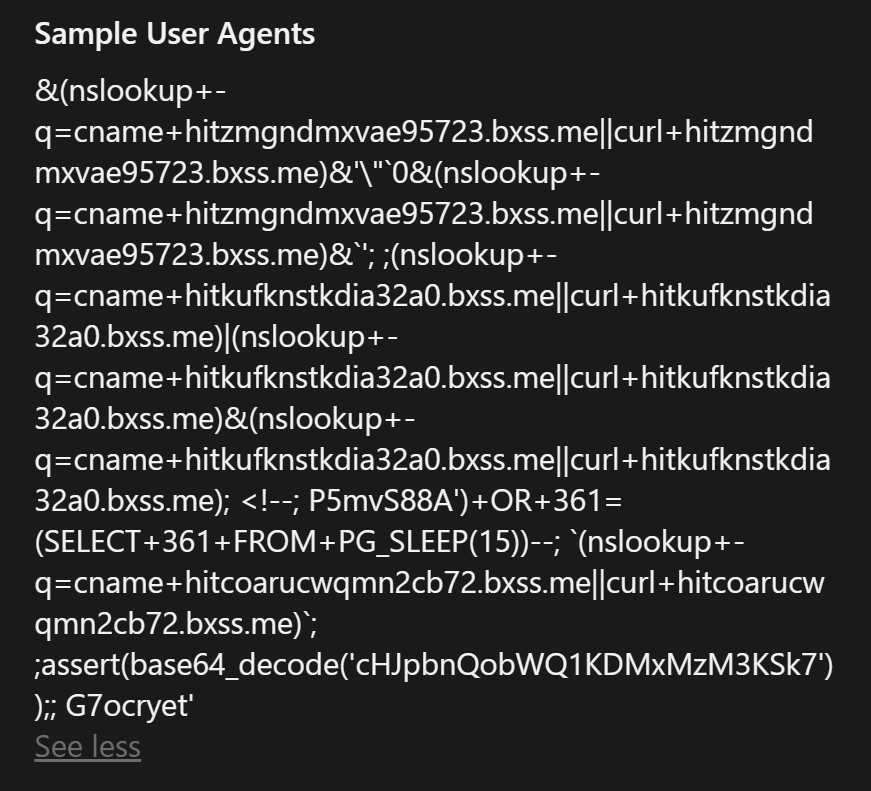
Quite interesting user agent in the request:
From the Alerts for Azure App Service we get good explanation for this:
Azure App Service activity log indicates requests with suspicious user agent. This behavior can indicate on attempts to exploit a vulnerability in your App Service application.
This is something that I’ll monitor because it seems to be one time thing for now.
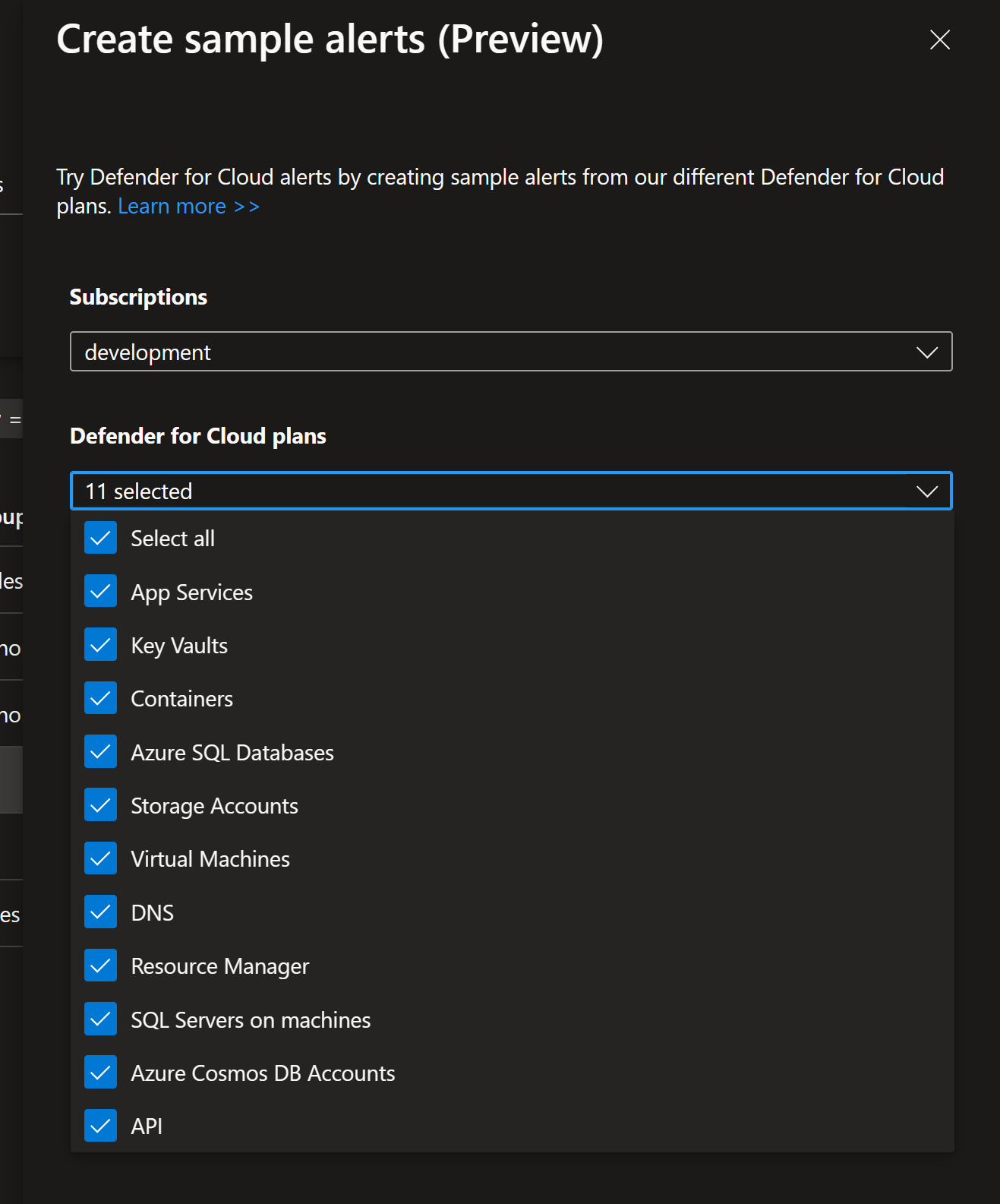
Sample alerts
You can also use Sample alerts functionality to generate alerts for your environment:
Summary
I hope you got some idea how Microsoft Defender for Cloud can help you to find these issues and alert you about these findings. Now it’s your turn to take it for a spin and learn more about it.
I hope you find this useful!